Employee Security Awareness Training
Turn your employees into your strongest ransomware defense.

Equip Your Employees to Identify Threats
Did you know that human error is responsible for over 95% of today's cyber attacks and breaches?
But what if you could teach your employees the traits of phishing, spear phishing, malware, ransomware and social engineering and how to apply this knowledge in their day-to-day job?
Centre helps you get the most out of your investment by customizing course curriculums, monitoring completion and satisfactory scores, and putting it to the test with simulated phishing campaigns.
Continuous Training Plan
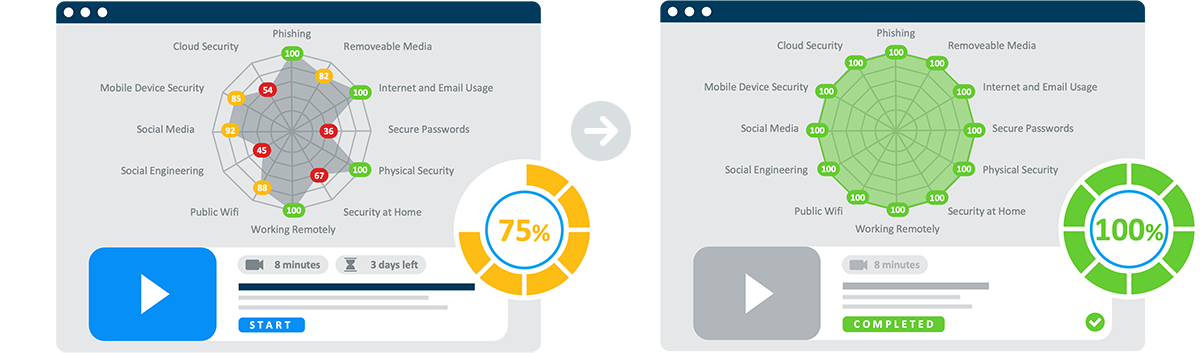
Managed curriculum of quick "micro-trainings" tailored to both individual employees and business compliance requirements.
Improved Awareness and Performance
Simulated email phishing campaigns that improve and practice employee response and ensures vigilance.
See Insights with Key Training Indicators
Advanced reporting with stats and graphs to quickly identify training effectiveness.
Security Portal with Recommendations
A Proven Approach for Fighting Ransomware
Equip, train, and test your employees to stay on their toes, keeping cybersecurity top of mind.
What makes our Employee Security Awareness program better
Train Your Users
Tailored "micro-trainings" only take about 10 minutes and address individual gaps.
Phish Your Users
Fully automated simulated phishing attacks to ensure employees are staying vigilant.
See the Results
User-friendly reporting that includes stats and graphs for both security awareness training and phishing.
"Engaging, easy-to-read content and interactive videos make the training enjoyable and effective."
Business Support Associate
Accounting Firm in San Antonio, Texas
"A simple and engaging platform that makes learning accessible and even fun."
HR Manager
Manufacturing Company in Tulsa, Oklahoma
Stop Future Threats Today
Safe-guard your business through managed curriculum and training.
Enterprise
Experience
People, process, and technology that scales cybersecurity and operations
Personalized
Service
We get to know your business and people for a true partnership experience
Local
Touch
In-person collaboration and support delivered with genuine hospitality and professionalism
Frequently Asked Questions About Security Awareness Training
What is security awareness training?
These trainings are given to all employees in your organization with the goal of helping your team identify data threats and avoid them. The ultimate goal is to stop human error resulting in a breach.
Why is security awareness training required for most cyber insurance policies?
The simple answer is because many breaches happen because of human error. Insurance is there to be a safety net in the eventuality of a cybersecurity attack regardless of where it comes from. In order to insure you, most policies want to make sure they don't have to worry that your employees are the very preventable reason why you're experiencing a breach.
Does HIPAA require security awareness training?
Yes. The HIPAA Security Rule requires periodic employee security training updates (although they don't define what's considered periodic). Sometimes healthcare businesses like yours think they're compliant but don't find out until they're formally audited that they're not meeting formal requirements. Don't be that business! Stay up to date!
What is the difference between HIPAA awareness and security awareness training?
HIPAA is designed to give an overview of only HIPAA requirements while Employee Security Awareness Trainings from Centre focuses on HIPAA and other security awareness content unique to healthcare.
What topics should be included in security awareness training?
Important topics that are common ways ransomware attacks are through:
- Phishing Attacks (via email)
- Smishing Attacks (vis text messages)
- Removable Media (like USBs)
- Password Best Practices and MFA Security
- Physical Security (like badges)
- Working Remotely and Working from Home
- Public Wi-Fi Best Practices
- Social Media and Social Engineering
How often should you conduct security awareness training?
Unfortunately, the more time in between trainings, the less an employee retains from it. Our quick "micro-training" modules are delivered monthly (or more often based on your organization's compliance needs) to make training a regular part of an employee's responsibilities without overwhelming them.
Security Awareness Topics + News
Learn more about how security awareness protects your organization from cybersecurity threats.














